INDIAN ARMED FORCES CHIEFS ON OUR RELENTLESS AND FOCUSED PUBLISHING EFFORTS

The insightful articles, inspiring narrations and analytical perspectives presented by the Editorial Team, establish an alluring connect with the reader. My compliments and best wishes to SP Guide Publications.

"Over the past 60 years, the growth of SP Guide Publications has mirrored the rising stature of Indian Navy. Its well-researched and informative magazines on Defence and Aerospace sector have served to shape an educated opinion of our military personnel, policy makers and the public alike. I wish SP's Publication team continued success, fair winds and following seas in all future endeavour!"

Since, its inception in 1964, SP Guide Publications has consistently demonstrated commitment to high-quality journalism in the aerospace and defence sectors, earning a well-deserved reputation as Asia's largest media house in this domain. I wish SP Guide Publications continued success in its pursuit of excellence.
- Indian Air Force Aims for Full Indigenous Inventory by 2047 — Air Chief Marshal A.P. Singh
- General Upendra Dwivedi takes over as the Chief of the Army Staff
- Rajnath Singh assumes charge as Defence Minister for the second consecutive term
- Admiral Dinesh K. Tripathi assumes Command of the Indian Navy as 26th Chief of the Naval Staff
- Prime Minister witnesses 'Bharat Shakti' – a Tri-Services Firing and Manoeuvre Exercise in Pokhran, Rajasthan
Spam campaign focused on India
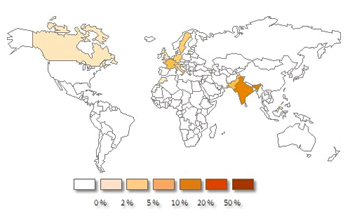
Symantec has observed that a recent malicious spam campaign focused on users in India. The e-mails contained a malicious attachment, detected as Spyware. Redpill, which is used by cyber criminals to steal confidential information. This includes credentials for social networking accounts, bank account details, e-mails written on compromised computers and screenshots.
A statement issued by Symantec said that upon opening the attached file, users receive an error message indicating that the file was corrupted. However, the malware is silently executed and has already begun to steal information, even as its malicious purpose remains hidden from the user. In the background, the malware installs itself on the compromised computer. It also creates a registry entry subsequent to which keystrokes are recorded and screenshots taken.
“The stolen information is sent to an e-mail account hardcoded into the programme. In our investigations we found details of the e-mail account used by the attacker to receive the stolen data—for instance, it received over 12,000 e-mails in March 2013,” said Abhijit Limaye, Director, Development, Security Response, Symantec.





